September 15, 2010 (Vol. 30, No. 16)
Kathy Liszewski
Latest Tools and Technologies Help Untangle a Broad and Diverse Network of Interactions
It is estimated that more than 30% of all protein-coding genes in the human genome are regulated by miRNAs. This significant role has resulted in a considerable amount of attention being paid to this family of noncoding RNA molecules.
Select Biosciences’ recent “RNAi and MiRNA Europe” meeting featured discussions on cutting-edge technologies for integrating miRNAs into the genome and for functionally analyzing expression. Insights to help unravel the complex picture of miRNA interactions, including modeling miRNA networks using high-tech tools of space-age cryptography and communications signal analysis, were also presented.
DNA integration is a powerful technology that enables disruption, modification, or replacement of an endogenous locus with a new gene. That same technology can also be utilized with miRNA genes.
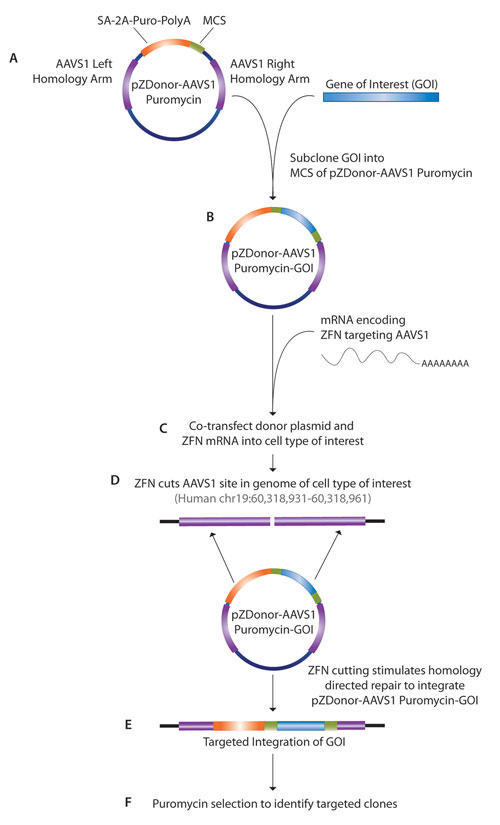
In the past, most genes were randomly integrated into the host’s genome. “The problem is that this can produce off-target effects,” noted Kevin Forbes, Ph.D., senior R&D scientist at Sigma-Aldrich. Dr. Forbes said that the company’s CompoZr™ Zinc Finger Nuclease (ZFN) technology allows the site-specific integration of any gene, including those of miRNA.
“We’ve seen a lot of interest in this new technology because most people have used lentiviral systems that integrate randomly. ZFN technology employs a pair of well-validated nuclear ‘safe harbor’ sites. We know exactly where in the genome it goes and can rule out positional effects.”
Dr. Forbes has expressed miRNA genes from the human genome utilizing the company’s CompoZr Targeted Integration Kit that places a specified gene into the adeno-associated virus (AAVS1) site on human chromosome 19. ZFNs create a double-stranded break that can be repaired by the supplied pZDonor plasmid, since it has homologous arms to the AAVS1 site at either end of a multiple cloning site. Thus, the repair takes place and inserts the gene between the homologous arms.
Scientists at Sigma-Aldrich have focused many of their efforts on miRNAs related to cancer metastasis. “Using this technology we provided the first proof-of-concept that we can express specific miRNAs at a known human locus. We expect many applications for both research and therapeutics. Certainly, a key benefit is that we can now provide a well-characterized site found in every human cell for targeted integration.”
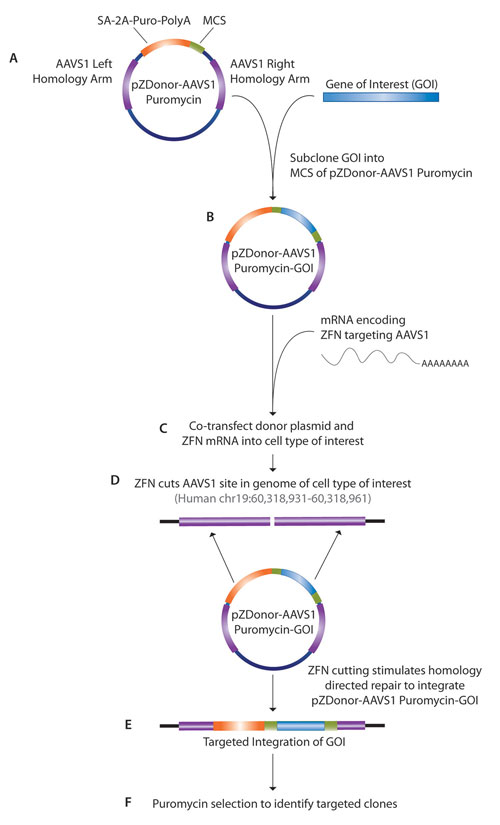
Sigma-Aldrich reports that its CompoZr Zinc Finger Nuclease (ZFN) technology allows for the site-specific integration of any gene, including those of miRNA.
miRNA Expression
To better understand miRNA contributions to normal and diseased cell physiology, Thermo Fisher Scientific has developed what it says is a unique approach for expressing mature miRNAs. According to Annaleen Vermeulen, Ph.D., senior scientist, there are several approaches for functionally analyzing miRNAs.
“While synthetic miRNA mimics work well for transient overexpression in vitro, some cells are resistant to the delivery methods required, such as lipid transfection. Lentiviral vectors can overcome this limitation, but expression presents other challenges. Existing approaches rely on expression of the native primary miRNA, which is subject to innate regulation by the cell and can yield ambiguous results across cell types and conditions.”
To address the issues posed by inconsistent processing of expressed miRNA, the company developed a novel design strategy. “Our latest miRNA technology, the miRIDIAN® shMIMIC™ Lentiviral miRNA, embeds each human mature miRNA annotated in the miRBase into a highly optimized, universal primary miRNA scaffold. As such, we are able to maintain critical secondary structural elements for the consistent, reproducible processing of mature miRNA.”
Alex Amiet, senior product manager, RNAi, explained that “each shMIMIC miRNA has been designed, cloned, and packaged into lentiviral particles so the researcher can transduce into biologically relevant cells, including difficult-to-transfect primary, neuronal, and stem cells.
“The optimized, universal primary miRNA scaffold ensures robust enzymatic processing and transport of miRNA in a consistent manner within any given cell. Additionally, because the lentiviral vector allows integration of the shMIMIC miRNA into the host cell genome, researchers can create stable cell lines.”
Amiet noted that investigators still need to optimize certain parameters such as cell number and viral transduction conditions. “Overall, it is fairly straightforward, since we provide concentrated lentiviral particles. For the future, we may expand the collection to include mouse and rat miRNAs. At present, since miRNAs are evolutionarily conserved among mammals, many human shMIMIC miRNAs may be applicable in rodent models.”
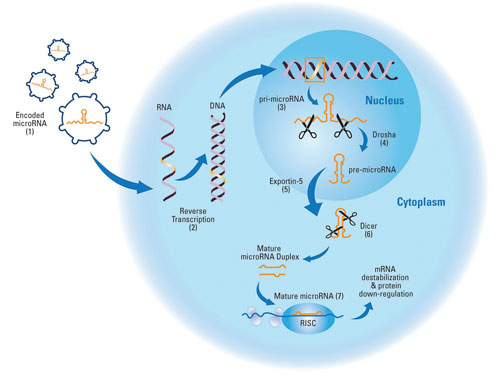
Borrowing the endogenous pathway that processes host-encoded microRNA transcripts to overexpress functional mature microRNA [Thermo Fisher Scientific]
Seeking Specificity
Determining the specific targets, phenotypes, and pathways impacted by miRNAs can be challenging given the state of the art and the complexity of such interactions. Traditional approaches often utilize miRNA inhibitors and/or mimics for functional analyses.
“The problem with these types of studies is that a miRNA can regulate a large number of different targets,” noted Martin Kreutz, a scientist at Qiagen. “Using a miRNA mimic or inhibitor for functional analysis affects the regulation of all these targets, and one cannot determine how the regulation of a specific target contributes to a phenotype.”
To address this vexing issue, Qiagen developed a new tool for functional analysis called miScript Target Protectors. The Target Protector is a single-stranded modified RNA that is transfected into cells where it binds to and thus blocks the miRNA binding site of a specific target gene. This allows characterization of the effects of downregulation of a single target, while leaving other targets unaffected.
Applications include verifying miRNA binding sites, determining miRNA roles in specific pathways, characterizing regulation of the gene of interest, and confirming results obtained in other experiments, Kreutz said. “We’ve had a lot of interest in this since there is no other such system on the market.”
Investigators must lay some groundwork prior to using the technology, however. “It is necessary for the scientist to be aware of the particular miRNA target they want to study. Secondly, they must decide on a binding site they trust. We can give advice on how to identify potential binding sites, but often the researcher is already aware of what binding site may be involved. If more than one site is suspected, it would be wise to perform studies of both.
“Due to the complex miRNA binding behavior, specialized tools are necessary to investigate the effects of a single miRNA target interaction.” Kreutz cited the example of a study in which the Target Protector for the ADAR gene and a mimic for miR-1 were co-transfected into HeLa cells.
“The miRNA called miR-1 downregulates expression of both ADAR and HDAC4. As assessed by Western blot, after 72 hours, the Target Protector specifically protected only ADAR from downregulation by miR-1, not HDAC4. This both verified the binding site targeted and demonstrates how this technology can be useful in deciphering the relevant players that contribute to a particular phenotype.”
Cryptography and miRNAs
You may have never thought of molecular biology as an intriguing cloak and dagger operation complete with coded messages and cryptic communications, but that may change soon. Harry Shaw, staff engineer at National Aeronautics and Space Administration (NASA), is developing a model to attack problems in molecular biology using cryptography tools and communication signals analysis.
“Many types of information are coded, encrypted, and involved in network security. There are similarities between biology and information processing in the real world. For example, in cryptography one looks at ways to provide two services: confidentiality in the form of codes and authentication, which validates the credentials of the sender and ensures that the message is unaltered in transmission.”
According to Shaw, analogous molecular biological processes also seek authentication in recognizing the correct connections via structure and sequence and confidentiality in the form of codes, such as the genetic code, the protein alphabet code of 20 amino acids, and the histone code.
For example, a gene is encrypted when it is not expressed and is decrypted when activated and undergoes transcription, and then subsequently reverts to the encrypted form.
“miRNAs are short sections of noncoding RNAs that induce a broad pattern of protein translation modifications,” Shaw said. Modeling miRNA can be informative. The approach involves building a model employing virtual senders and receivers using miRNA and messenger RNA (mRNA) sequences as message traffic.
A communication channel model can be created to provide a physical context for the message traffic, much like a wireless communications channel. The model allows for coding of secondary structure information on a probabilistic basis using entropy coding (already used in data-compression algorithms). Options for adding spectroscopic information to the encryption process are also being investigated.
The goal of these models is to improve predictions of miRNA and mRNA seed-target binding. The process is extensible to include higher levels of complexity such as inclusion of RNA-induced silencing complex structures.
“Eventually, such models will require validation using functional assays. Once the models are validated and calibrated, the results will foster better ways to engineer miRNAs with more specific binding properties for mRNA. This could help to improve therapies that modulate gene expression,” Shaw added.
The field of miRNA is still young and evolving. Many challenges remain, yet as the methodology continues to advance, new understandings are expected to emerge and spawn potentially impressive therapeutic applications.